This is how I have it set up to be my IPv6 tunnel firewall
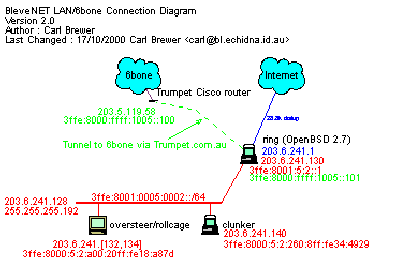
I have been allocated the IPv6 address space 3ffe:8001:0005::/48 from Trumpet.com.au (Thanks Peter!).
My tunnel endpoint details were provided by Peter as :
3ffe:8000:ffff:1005::100/64 Tunnel to Carl Brewer (Trumpet end) 203.5.119.58 3ffe:8000:ffff:1005::101/64 Tunnel to Carl Brewer (My (carl) end) 203.6.241.1The IPv4 address of my external gateway is 203.6.241.1 and the IP address of the tunnel endpoint is 203.5.119.58
This is what it looks like :

I have IPFilter running on the OpenBSD box, and this is how I made it play nicely :
First, I recompiled ipf and ipfstat with USE_INET6 defined in their makefiles. I'm not 100% sure if I had to do this, but after I did, ipfstat -6 started working, so I think I probably did!
THIS IS NOT CORRECT. OpenBSD does NOT enable IPv6 filtering using IPF. I have discussed this with Darren Reed, and the following is erronious. DO NOT USE THIS TO GET A FIREWALL WORKING on OpenBSD. Note however, that the following rules should work just fine on NetBSD.
Then, I changed my ipf.rules file, if you recall from
the "router" webpage, I had this :
pass in quick proto 41 from any to any pass out quick proto 41 from any to anyI now have this :
# IPv6 tunnel ... 203.5.119.58 -> 203.6.241.1 pass in quick on ppp0 proto 41 from 203.5.119.58 to 203.6.241.1Ie, I'm not letting just anyone in who's talking IPv6 anymore.
And, once I did that, I wanted to be able to use IPv6 firewalling as
well, so I created a new file : /etc/ipf6.rules, which looks like this :
# incoming email and web traffic pass out quick on ep1 proto tcp from any to 3ffe:8001:5:2:a00:20ff:fe18:a87d port = smtp keep state pass out quick on ep1 proto tcp from any to 3ffe:8001:5:2:a00:20ff:fe18:a87d port = auth keep state # DNS ... I run a BIND 9 DNS server for testing pass in quick proto tcp from any to any port = 53 keep state pass in quick proto udp from any to any port = 53 keep state # ssh only to rollcage pass out quick on ep1 proto tcp from any to 3ffe:8001:5:2:a00:20ff:fe18:a87d port = 22 keep state # irc both ways # pass in quick proto tcp from any to any port = 6667 keep state # let everything out pass in quick on ep1 proto tcp from 3ffe:8001:5::0/48 to any keep state pass in quick on ep1 proto udp from 3ffe:8001:5::0/48 to any keep state pass in quick on ep1 proto ipv6-icmp from 3ffe:8001:5::0/48 to any keep state pass out quick on ep1 proto tcp from 3ffe:8001:5::0/48 to any port = ntp pass out quick on ep1 proto udp from 3ffe:8001:5::0/48 to any port = ntp # let loopback stuff work pass in quick on lo0 all pass out quick on lo0 all # finally, drop everything we haven't specifically allowed block in log quick from any to anyI then ran it up using
ipf -6 -f /etc/ipf6.rulesand it seems to work. OpenBSD doesn't seem to want to load ipf6.rules by default, but I added ipf -6 -f /etc/ipf6.rules to /etc/rc.local just after I set up my tunnel, and that seems to work just fine.